These Everyday Devices Can Be Hacked
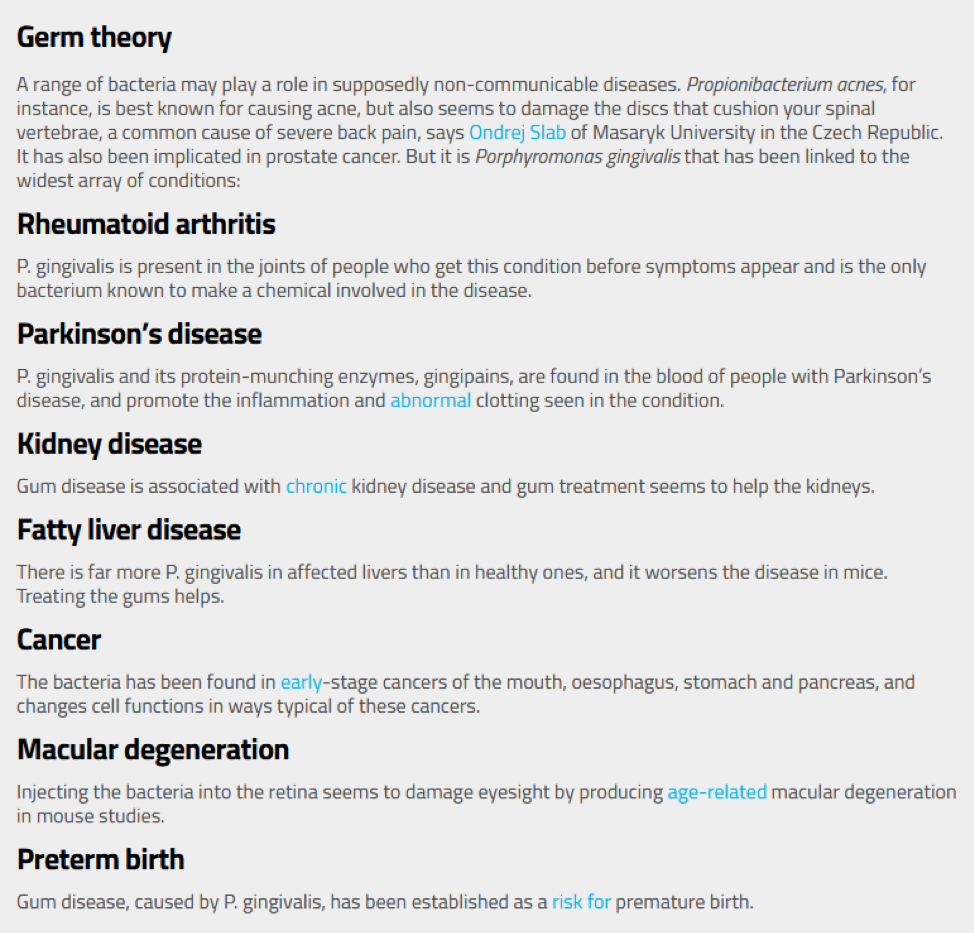
The internet of things (IoT) is responsible for many conveniences via embedded electronic devices, and many seniors are making use of these technologies. It is becoming increasingly common for everyday items like refrigerators, thermostats, and doorbells to be internet-connected making our homes and personal information subject to hacking. A hacker will subvert computer security for malicious purposes. Seniors who employ IoT devices for safety and convenience may be less wary of all the ways their devices can be compromised. If you are a senior or have a loved one who is, it is imperative to have them, or a trusted friend, update software from device manufacturers and routinely monitor their devices.
A Smart TV provides many hacking opportunities. The problem can be an annoying prankster blasting the volume control, switching channels, or even ordering movies you did not select. Or the hacker can also compromise your security and safety as your Smart TV is a gateway to other internet-connected devices in your home. TV apps can be data mined for credit card payment information since many manufacturers reuse default passwords, and users neglect to change them. Even companies who sell Smart TVs are now post-purchase monetizing the Smart TV by harvesting your information via data collection and using it for advertising and direct sales of entertainment to the consumer.
Digital Thermostats are a great way to keep heating and cooling costs down. However, a hacker who takes control of your thermostat can crank up the heat or cooling until the owner pays a ransom to regain control of the device. An older person can experience health consequences due to extremes temperatures as well as the anxiety and fear it breeds. Baby monitors are often connected to your home’s Wi-Fi network for the convenience of a mobile app to check the display at any time. Many homes use these monitors for seniors instead of small children. Typically, people do not change the default password on the monitor, meaning that it is visible to the network. A hacker can scan transmitting internet protocol or IP addresses (numerical labels assigned to every device that connects to a computer). Once they have your IP data, they can find the baby monitor and watch you or your loved one at any time. For better protection shop for baby monitors that are made to be invisible to scans. If you have a Samsung smart refrigerator, it can be hacked. The wiring in the fridge leaves the new owner’s Google login credentials out in the wild for a hacker to grab and then infiltrate your home’s IoT devices.
Smart cameras have vulnerability issues allowing a hacker to remotely access audio and video feeds. Be sure to keep track of all of your IoT devices that are network connected. Actively seek out all software and firmware updates for maximum protection against hackers. Smart voice-activated speakers like Alexa, Google, Echo, and many more open up every conversation you have in your home to be monitored by a hacker. Without even being aware, you can divulge sensitive information like doctor appointments, luncheon dates, and upcoming trips. Even your bank account and credit card information can be compromised. If your home security system is connected to your voice-activated speaker, a hacker can turn it off and enter your home.
Even pacemakers are subject to hacking however improbable that might seem. Anyone with bad intentions toward you can remotely change the pace of your heartbeat, which can even result in your death. Implanted medical devices, in general, are now subject to more stringent controls that use code to secure data and instructions in these devices and monitor them in real-time. Talk with your medical professional to know that you are protected against medical hackers.
Default passwords need to change in order to protect your devices from hackers. Most internet-connected devices have simple default passwords, and a search run on the name brand of a device will often yield the manufacturer’s default password. When you change your password, make it very strong, and use unique passwords for each device. Out of convenience, many seniors will use the same password for everything. In this case, if a hacker gets into one device, they can be in all of them if you do not use different passwords.
Cell phones, home Wi-Fi routers, and even landline voicemail are susceptible to hacking. Inexpensive signal-proof cases are good to use for protection when you are out in public. It is possible for a hacker to clone your phone in seconds while standing next to you and they will get everything you store on your phone. Home Wi-Fi routers must be up to date on all software and firmware, and a unique, strong password can help protect you from hackers. Once a hacker gains access, all of your devices connected via the internet of things have been compromised as the router is the nerve center of your digital footprint. Many seniors still like to have a landline telephone and its associated voicemail. Passwords to access voicemail must be very secure, or a hacker can listen in to your conversations as well as delete potentially important messages.
All senior grandparents love pictures of their family to be proudly displayed. Picture frames that are digital and allow you to scroll through photos or change an art display with the swipe of a hand are vulnerable. If your frame becomes hacked, a thief can discern non-active times in your home by the frame’s ambient light sensors and can plan a robbery while you are away.
Garage door openers are also able to be hacked if you have a newer smart version device. A hacker can monitor garage door activity and identify times when you are not at home. It is very convenient for a burglar to avoid encountering people during a robbery. Be sure to update a manufacturer’s default password setting to something difficult to break, and a would-be robber will move to an easier target.
Cars and Self-driving cars can be hacked. It doesn’t take a lot of equipment to break into and start a vehicle, even disabling the alarm system. Car thieves now employ sophisticated hacking technology, especially when they must bypass the electronic anti-theft systems. If a self-driving car is hacked, the attacker can take direct control over the throttle, brake, and steering while remaining anonymous as to their identity and location creating a very dangerous scenario.
Convenience comes at a cost to your privacy when using the internet of things. Taking the necessary steps to protect your devices from hackers is of paramount importance. Once secure procedures are in place, it is crucial to monitor for suspicious activity that can lead to robbery, electronic banking theft, and more. Taking control of your internet-enabled devices is essential to protect your home and your strategy for aging successfully. No one wants to be victimized by unwanted hackers.
If you have any questions or need guidance with your planning or planning for a loved one, please don’t hesitate to contact our Ruston, Louisiana office by calling us at (318) 255-1760.